Mixpanel Security Breach November 2025: What Startups Need to Know
Mixpanel experienced a significant security breach in November 2025, resulting in unauthorized access to OpenAI API user data and raising critical questions about third-party analytics vendor security. Therefore, this mixpanel incident demonstrates how even established platforms with SOC 2 Type II certification can face sophisticated cyberattacks. Moreover, the mixpanel breach affected limited user profile information without compromising passwords or API keys, yet it exposed vulnerabilities in vendor management practices. Consequently, startups relying on mixpanel or similar analytics providers must reevaluate their third-party security protocols and understand the November 2025 mixpanel breach implications for their own data protection strategies.

Mixpanel Security Breach: November 2025 OpenAI User Data Exposure
Understanding Mixpanel: The Analytics Platform Behind the Breach
Mixpanel operates as one of the technology industry’s most prominent product analytics platforms, serving thousands of companies including Samsung, BMW, Intuit, and major startups globally. Specifically, mixpanel specializes in event-based analytics tracking user behavior across web and mobile applications. Therefore, companies integrate mixpanel to understand feature adoption, user retention, funnel conversion, and product engagement patterns through detailed behavioral data collection.
Unlike traditional page-view analytics, mixpanel captures granular user interactions—button clicks, feature usage, scroll depth, and custom events—enabling product teams to make data-driven decisions. Additionally, mixpanel offers real-time dashboards, advanced cohort analysis, retention curves, and funnel visualization capabilities that help startups optimize product experiences. Moreover, mixpanel provides a generous free tier supporting up to 1 million monthly events, making it particularly attractive for early-stage companies seeking sophisticated analytics without substantial upfront investment.
How Mixpanel Fits Into Modern Product Development
Product managers and growth teams utilize mixpanel to answer critical business questions: Which features drive long-term retention? Where do users abandon onboarding flows? What user segments convert to paid customers? Consequently, mixpanel has become integral infrastructure for data-driven product development, processing billions of events monthly across its customer base. Therefore, any mixpanel security incident creates ripple effects across the entire technology ecosystem, affecting not just the analytics provider but all companies depending on its services.
November 2025 Mixpanel Breach: Timeline and Technical Details
On November 9, 2025, unauthorized attackers gained access to a portion of mixpanel systems, successfully exporting datasets containing customer identifiable and analytics information. Subsequently, mixpanel became aware of the intrusion and began internal security investigations. Therefore, on November 25, 2025, mixpanel formally notified OpenAI about the breach after determining that OpenAI API user data had been compromised through the mixpanel platform.
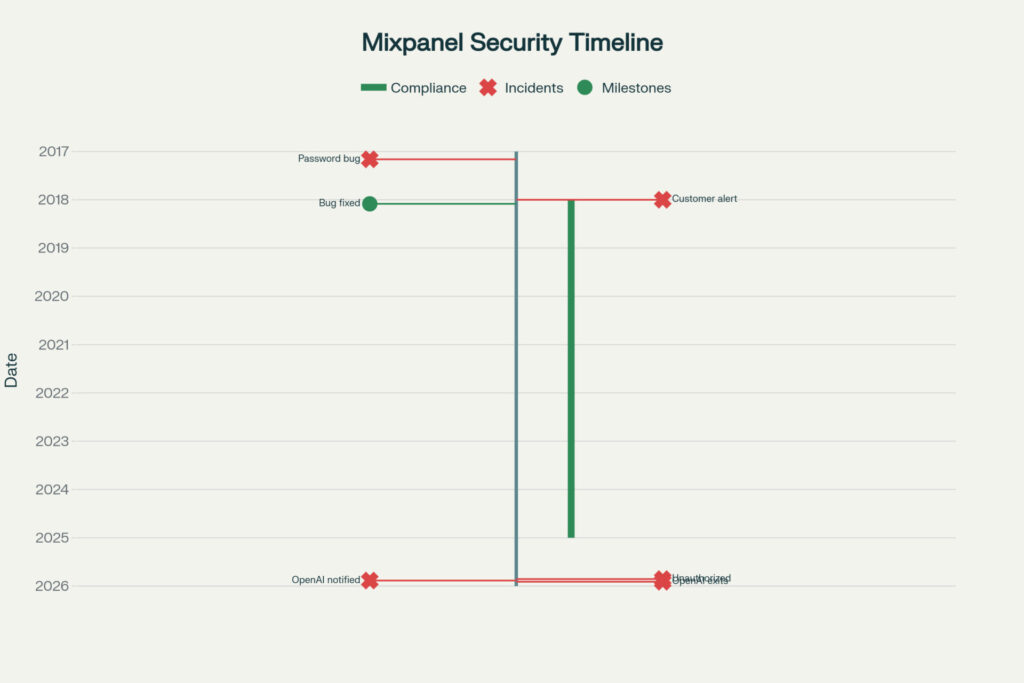
Mixpanel-security-timeline-from-2017-2025-showing-password-capture-bug-in-2018-and-recent-November-2025-breach-affecting-OpenAI-API-users’-data
Specifically, OpenAI utilized mixpanel exclusively for web analytics on the frontend of its API product interface at platform.openai.com. Therefore, the mixpanel breach affected only OpenAI API users, not ChatGPT consumers or other OpenAI product users. Moreover, the security incident occurred within mixpanel infrastructure rather than OpenAI’s core systems. Consequently, critical data including chat content, API requests, API usage metrics, passwords, credentials, API keys, payment details, and government identification remained completely secure and uncompromised.
Checkout Our Latest Services

Lead Generation & Sales Acceleration (Paid Ads)

Government Grant Application (Per Scheme)

Complete Fundraising Package - Investor Ready Documents
Govt Grant Application (6 Months Package)

MSME / UDYAM Registration

Govt Grants Application Package (1 Year)

Organic Social Media Management

Brand Kit (Covered Everything)

Brand Awareness Campaigns - 3 Month Visibility Program

- Select options This product has multiple variants. The options may be chosen on the product page
Website Development (WordPress)
What Data Did the Mixpanel Breach Expose?
The mixpanel attacker successfully exported limited user profile and analytics information associated with platform.openai.com usage. Specifically, the compromised mixpanel dataset included:
User names provided to OpenAI during API account registration
Email addresses linked to API accounts
Coarse approximate location derived from browser data (city, state, country level)
Operating system and browser information used to access API accounts
Referring websites showing how users navigated to the platform
Organization and User IDs associated with API accounts
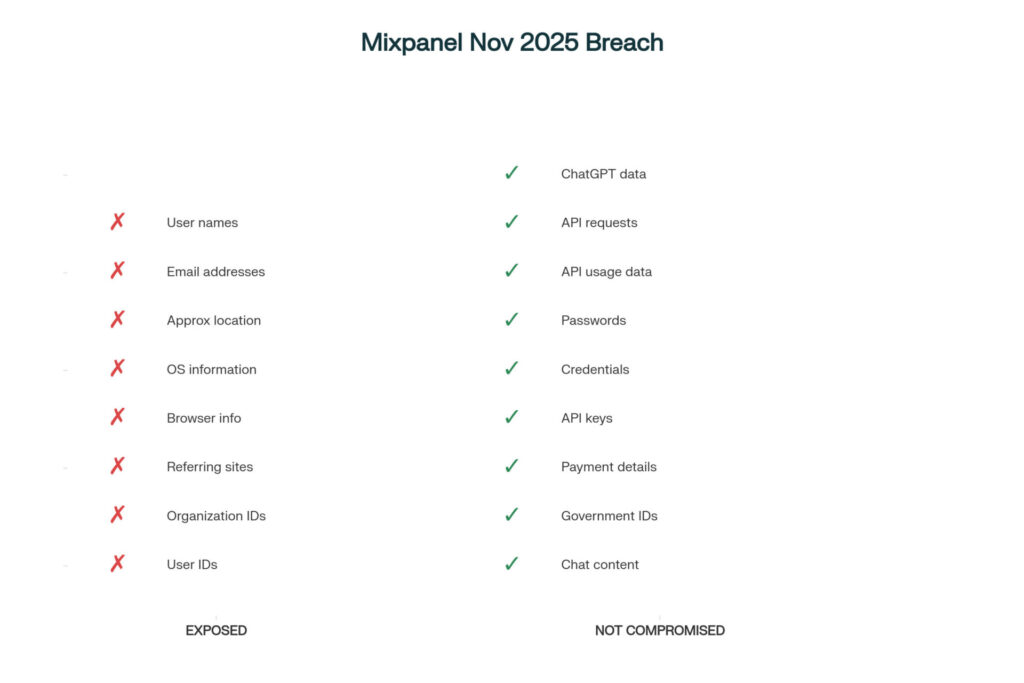
Therefore, while the mixpanel breach exposed personally identifiable information that could enable phishing attacks, it did not compromise authentication credentials or financial data. Moreover, OpenAI confirmed finding no evidence of actual misuse of the exposed mixpanel data, though monitoring continues for potential malicious activity.
OpenAI’s Response: Terminating Mixpanel and Strengthening Vendor Security
Following the mixpanel breach notification, OpenAI moved decisively to address the security incident. First, OpenAI immediately removed mixpanel from all production services following comprehensive security investigation. Therefore, OpenAI terminated its entire mixpanel relationship rather than attempting remediation, signaling zero tolerance for vendor security failures. Additionally, OpenAI initiated direct email notifications to all affected organizations, administrators, and individual API users, providing transparency about the mixpanel breach impact.
Furthermore, OpenAI announced conducting expanded security reviews across its complete vendor ecosystem, elevating security requirements for all third-party partners. Consequently, the mixpanel incident triggered systemic improvements in OpenAI’s vendor management practices, likely establishing new precedents for third-party security standards across the AI industry. Moreover, OpenAI explicitly stated it would not require password resets or API key rotations since the mixpanel breach did not compromise authentication credentials—a decision reflecting confidence that core security infrastructure remained intact.
User Protection Recommendations Following the Mixpanel Breach
Despite the limited nature of exposed data, OpenAI issued specific guidance helping API users protect themselves against potential exploitation of the mixpanel breach information:
Exercise Caution: Treat unexpected emails or messages with heightened suspicion, particularly those containing links or file attachments claiming to originate from OpenAI or mixpanel.
Verify Official Domains: Double-check that communications genuinely originate from official company domains rather than sophisticated impersonation attempts.
Protect Credentials: Remember that neither OpenAI nor mixpanel will ever request passwords, API keys, or verification codes via email, text message, or chat—any such requests indicate phishing attempts exploiting the breach.
Enable Multi-Factor Authentication: While the mixpanel breach didn’t expose credentials, enabling MFA at the single sign-on layer provides critical protection against unauthorized access attempts.
Mixpanel’s Security History: Not the First Incident
Unfortunately, the November 2025 mixpanel breach represents the second major security incident in the platform’s history. Previously, in February 2018, mixpanel experienced a password collection bug affecting approximately 25% of customers when its Autotrack feature inadvertently captured password fields due to unexpected interactions with the React JavaScript library.
Specifically, a March 2017 change to React’s open-source code clashed with how mixpanel Autotrack functionality operated, causing the platform to collect hidden and password field values it wasn’t designed to capture. Therefore, for nine months, mixpanel inadvertently collected customer passwords before a client alerted the company in January 2018. Consequently, mixpanel began filtering and destroying collected passwords by January 9, 2018, notifying affected customers via email on February 1, 2018.
However, independent researchers subsequently discovered that mixpanel continued capturing passwords on some websites even after the purported fix, revealing fundamental limitations in blacklist-based filtering approaches to prevent sensitive data collection. Moreover, Princeton University researchers identified password leaks to multiple analytics providers beyond mixpanel, demonstrating industry-wide challenges with wholesale data collection strategies that attempt filtering sensitive information after capture rather than preventing collection at the source.
Why the Mixpanel Breach Matters for Startups
The mixpanel November 2025 security incident carries profound implications for startups and technology companies across several dimensions:
Third-Party Vendor Risk Management
First, the mixpanel breach demonstrates that even established, well-funded analytics platforms with SOC 2 Type II certification, ISO 27001 compliance, and GDPR adherence can experience sophisticated cyberattacks. Therefore, startups cannot assume third-party vendors maintain impenetrable security simply because they possess industry-standard certifications. Moreover, vendor security represents an ongoing risk management challenge requiring continuous monitoring rather than one-time due diligence during initial selection.
Consequently, startups should implement comprehensive vendor security assessment frameworks evaluating not just certifications but also incident response capabilities, breach notification timelines, insurance coverage, and contractual liability provisions. Additionally, companies should maintain vendor risk registers documenting which third parties access what data categories, enabling rapid response when breaches occur.
Data Minimization Principles
Second, the mixpanel incident validates data minimization principles advocated by privacy regulations like GDPR and CCPA. Specifically, OpenAI’s use of mixpanel exclusively for frontend analytics on platform.openai.com rather than across all products limited breach impact to API users only. Therefore, restricting third-party analytics to specific, necessary contexts rather than deploying them universally reduces exposure when security incidents inevitably occur.
Moreover, startups should critically evaluate what data they actually need to collect versus what analytics platforms can theoretically capture. For instance, approximate location data derived from browser information might satisfy analytics requirements without collecting precise GPS coordinates. Similarly, anonymized user identifiers can enable behavioral analysis without exposing personal email addresses to third-party platforms.
The Build vs. Buy Decision for Analytics
Third, the mixpanel breach may prompt some startups to reconsider whether they should build proprietary analytics infrastructure rather than relying on third-party platforms. Specifically, companies handling highly sensitive data—healthcare records, financial transactions, government information—might determine that the convenience of platforms like mixpanel doesn’t justify the vendor risk exposure.
However, building custom analytics infrastructure requires substantial engineering investment, ongoing maintenance, and expertise that early-stage startups typically lack. Therefore, most companies will continue utilizing platforms like mixpanel while implementing stronger data governance controls, vendor management practices, and incident response preparedness.
Mixpanel’s Security Capabilities and Compliance
Despite the November 2025 breach, mixpanel maintains robust security infrastructure and compliance certifications that position it as a leader among analytics providers:
SOC 2 Type II Certification: Mixpanel undergoes independent audits verifying that security controls operate effectively over extended periods.
ISO 27001 and ISO 27701 Certification: Mixpanel complies with international standards for information security management systems and privacy information management.
GDPR and CCPA Compliance: Mixpanel provides deletion APIs, data retrieval mechanisms, and user opt-out capabilities supporting privacy regulation compliance.
Encryption Standards: Mixpanel encrypts data in transit using HTTPS/TLS protocols and at rest using AES-256 encryption standards.
European and Indian Data Residency: Mixpanel offers regional data residency programs ensuring customer data remains within EU or India boundaries as required.
Access Controls: Mixpanel implements role-based access control and conducts regular access log audits limiting who can access customer data.
Therefore, the mixpanel platform maintains industry-standard security practices. However, the November 2025 breach demonstrates that even comprehensive security programs cannot guarantee immunity from sophisticated attackers who successfully penetrate defenses.
What Startups Should Do Now
In light of the mixpanel November 2025 breach, startups should take several immediate actions:
Audit Current Mixpanel Usage
First, companies currently using mixpanel should audit exactly what data they send to the platform. Specifically, review event tracking implementations to ensure no accidentally captured sensitive information—passwords, credit card numbers, social security numbers, health data—flows to mixpanel through poorly configured tracking code. Moreover, implement mixpanel data filtering capabilities that prevent sensitive fields from reaching the platform even if accidentally included in tracking calls.
Review Vendor Security Agreements
Second, examine contracts with mixpanel and other third-party vendors to understand breach notification obligations, liability limitations, and indemnification provisions. Therefore, if current agreements lack strong vendor liability clauses or rapid breach notification requirements, negotiate amendments or consider alternative providers offering more favorable security terms.
Implement Defense in Depth
Third, adopt defense-in-depth strategies assuming that individual security controls will eventually fail. Specifically, combine multiple protective layers—encryption, access controls, network segmentation, monitoring, incident response—so that single point failures don’t catastrophically compromise entire systems. Moreover, regularly test incident response procedures through tabletop exercises simulating scenarios like the mixpanel breach.
Alternative Analytics Platforms to Mixpanel
Startups concerned about the mixpanel breach might evaluate alternative analytics platforms offering different security profiles:
Amplitude: Direct mixpanel competitor offering similar event-based analytics with SOC 2 Type II certification and enterprise security features.
Heap: Provides autocapture functionality reducing manual event instrumentation while offering session replay and heatmap capabilities.
PostHog: Open-source analytics platform enabling self-hosted deployment, giving companies complete control over data storage and security.
Google Analytics 4: Free analytics solution with Google’s security infrastructure, though offering less product-specific functionality than mixpanel.
However, all third-party platforms carry inherent vendor risk. Therefore, the decision should balance security requirements against analytical capabilities, pricing, and implementation complexity rather than assuming any platform guarantees perfect security.
Conclusion: Learning from the Mixpanel Breach
The November 2025 mixpanel security incident exposing OpenAI API user data provides crucial lessons for startups navigating third-party vendor relationships. Specifically, even industry-leading analytics platforms with comprehensive compliance certifications face sophisticated cyberattacks that can compromise customer data. Therefore, startups must implement robust vendor risk management frameworks, data minimization practices, and defense-in-depth security strategies rather than relying solely on vendor certifications.
Moreover, the mixpanel breach demonstrates the importance of limiting third-party data access to only essential information, restricting analytics deployment to specific product contexts, and maintaining rapid incident response capabilities. Consequently, while platforms like mixpanel deliver substantial value through behavioral analytics and product insights, companies must balance convenience against inherent security risks associated with sharing customer data with external providers.
Learn More About Vendor Security:
Nitesh
Founder @ GrowthMandi, JobsMandi, StartUpMandi. Working in various Domains since 2017. Like, Sales & Marketing, Website Development, Graphic Designing, Digital Marketing, SEO, Business Development. Hobby: Research & Innovation, Photography, Travelling, Cooking.